Introduction to Crypto AML compliance and DeFi activity banks
More than $2 billion in crypto was stolen in 2025, with stablecoins accounting for over 60% of identified illicit activity, which brings crypto movement closer to the banking system than traditional monitoring frameworks were designed to address.
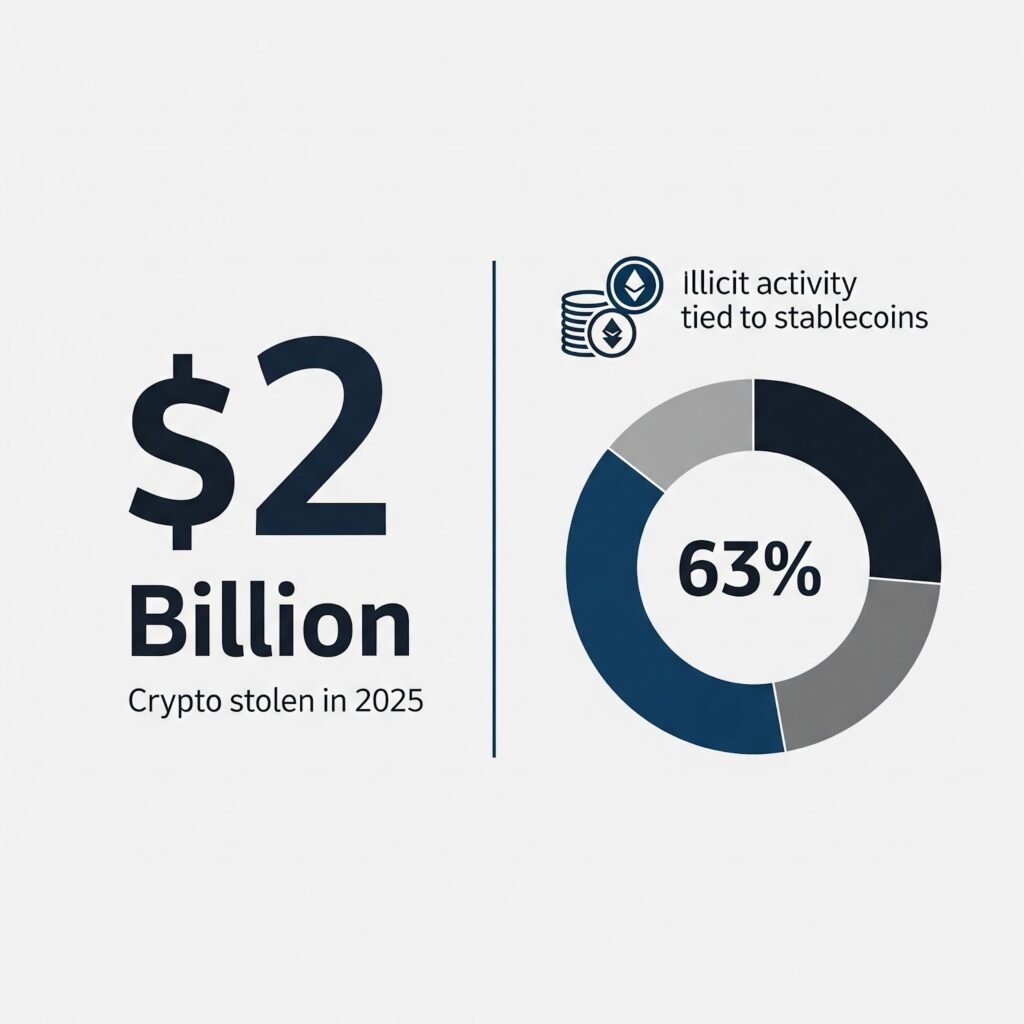
The problem is that crypto movement across ephemeral wallets, mixers, and automated DeFi channels leaves little for banks to examine, as attribution is lost before funds reach a customer account. Because of this limited visibility, deposits and transfers may appear routine even when they involve crypto. This loss of attribution is now a concern for supervisors globally, reflected in national risk assessments and international guidance on crypto and DeFi-related financial crime.
Traditional monitoring cannot reconstruct activity across these external wallets and DeFi services, making early identification of crypto-related risk extremely difficult.
| What this article covers: 🟣Why crypto AML compliance remains difficult when attribution is lost across wallets, relay services and DeFi channels. 🟣How crypto exposure sits inside deposits, transfers and commercial flows that resemble routine customer activity. 🟣Why individual institutions see too few confirmed cases to build reliable detection within their own environment. 🟣How collective model development brings hidden crypto and DeFi activity into view and strengthens investigative work. 🟣The supervisory expectations shaping crypto AML compliance in 2026. |
Why banks lose sight of crypto exposure inside their own activity
Most crypto transactions reach a bank only at the final step. By the time funds enter an account, the information needed to understand origin or routing has already been removed. Mixers and high-volume relay services erase the sequence investigators rely on to judge intent. And DeFi routing creates transfers that resemble settlement or cash management.
In essence, what enters the bank often appears routine until an analyst examines timing, direction, and customer profile. Even then, the indicators that point to crypto involvement can be incomplete.
Unfortunately, banks lose further visibility because virtual asset activity does not register cleanly inside existing controls:
- ➡Customers use offshore or unregistered services that never appear in standard counterparty data.
- ➡Small businesses handle flows that resemble brokerage activity without presenting as virtual asset providers.
These weaknesses impact the investigative workload. Analysts review alerts with limited attribution and little behavioral history. Plus, cases arrive without the full detail required to confirm or dismiss crypto involvement, which slows reviews and introduces uncertainty to decisions.
In short, crypto activity unfolds outside banking systems, then reappears without the context that investigators need to reach confident conclusions. Institutions encounter this gap during case review, escalation and program oversight.
Behaviors linked to crypto laundering that banks struggle to detect
Banks rarely see the behaviors that reveal crypto involvement in time to act. These behaviors emerge only when movement across wallets, intermediaries and services can be connected, and a single institution holds limited information. Many cases remain unresolved because the details needed to confirm or dismiss crypto involvement never reach investigators.
We tend to see several behaviors creating friction:
#1. Funds routed through exchanges with unclear licensing
Outbound transfers sometimes match the operating profile of offshore or unregistered exchanges. These entities do not appear in merchant or counterparty data, and the movement resembles routine customer activity until an analyst examines destination details.
#2. Relay activity associated with mixers or high volume transit services
These services break and reassemble flows, which removes the sequence investigators rely on. The bank receives a transaction with little attribution, and alerts escalate due to velocity or direction rather than insight into origin.
#3. Small business accounts that behave like virtual asset providers
Some accounts aggregate incoming transfers, forward balances quickly and show minimal operational spend. The pattern reflects an intermediary role linked to crypto conversion rather than classic structuring or cash-based layering activity.
#4. DeFi execution paths that resemble settlement
Automated routing and liquidity tools produce transfers that look like commercial settlements. The underlying execution logic sits outside the bank’s systems, and the movement blends into daily activity until an investigator reviews timing and direction.
These behaviors can trigger alerts based on speed, volume, or pass-through characteristics. What remains difficult is confirming intent and classifying the activity with confidence when upstream context sits outside the bank.
Why individual institutions cannot build reliable crypto AML compliance models alone
The core issue is that banks see too few confirmed crypto-related cases to build dependable detection on their own. Alerts are generated based on observable behavior, but investigators may not always have enough information to classify the activity with certainty. Attribution on origin, mixer involvement, or virtual asset service use arrives inconsistently, and often only after extensive review or law enforcement feedback.
This scarcity limits model development. Analysts cannot distinguish harmless outbound crypto movement from activity linked to laundering schemes without verified examples, and rules highlight unusual flows without explaining why they matter. Escalations grow while investigative learning advances slowly.
Similarly, insight is also distributed unevenly across the sector. One institution may confirm mixer involvement, another may identify an undeclared virtual asset provider, and a third may uncover relay activity linked to DeFi routing. None of this intelligence is visible to the others, which leaves each bank with an incomplete view of behaviors that appear across the industry.
These constraints impact the direction of crypto AML compliance, because the behaviors that determine intent surface only in confirmed cases, and no single institution sees enough of them to build a model that consistently identifies crypto exposure inside customer activity.
How collective model development helps institutions bring hidden crypto and DeFi activity into view
As you can tell by now, it’s easy to see the problem, so what’s the solution?
We think it all comes down to collaboration. Collective model development gives institutions access to learning they simply can’t generate within their own environment. Each confirmed case contributes intelligence that improves detection for every participant, and this takes place without exposing or moving client data.
Here’s a quick overview of what this looks like in practice:
| Area | Before | After |
| Investigative insight | Analysts review alerts with limited attribution and little upstream context. | Alerts arrive with behavioral detail informed by confirmed cases across institutions. |
| Mixer and relay activity | Escalations triggered mainly by velocity or volume. | Early identification supported by learning from verified mixer involvement. |
| Hidden virtual asset providers | Small business accounts acting as brokers remain unnoticed until late review. | Behavioral markers linked to VASP activity surface sooner. |
| DeFi involvement | Smart contract flows resemble settlement with limited context. | Routing behavior learned from closed cases helps flag DeFi-linked activity. |
| Model accuracy | Limited training data produces inconsistent detection. | A broader pool of outcomes strengthens detection across programs. |
| Regulatory confidence | Uneven treatment of similar crypto-related movement. | Clearer, more defensible visibility of crypto exposure. |
Evidently, collective learning is the most practical way to improve crypto AML compliance and focus investigative effort where it carries the most value.
Bringing hidden virtual asset service providers into view
Undeclared virtual asset activity can represent a significant source of crypto exposure inside banks. Accounts appear routine until investigators examine timing, volume and direction more closely.
Unregistered virtual asset providers often use commercial accounts. They operate through small businesses that receive frequent inbound transfers, forward balances quickly and show minimal operational spending. The activity resembles an intermediary role rather than a business serving a local market.
Personal accounts can act as conversion points. Individuals may receive funds from unrelated sources and relay them within short windows, which can trigger alerts based on pass-through or income mismatch. The challenge is determining whether the activity reflects crypto conversion, another financial crime typology, or legitimate behavior.
Resolved investigations across the sector make these behaviors easier to recognize. When learning from these outcomes is combined, consistent behavioral markers emerge. Banks can identify these accounts earlier, escalate fewer false leads and direct investigative effort toward cases that carry real crypto exposure.
Ultimately, stronger identification of hidden virtual asset providers gives institutions a clearer view of how value moves before it reaches their systems and helps strengthen the foundation of crypto AML compliance.

Better detection improves SAR quality and investigative efficiency
With this clearer view, insight into crypto involvement changes how investigative teams work. Cases that once arrived with little context now show earlier indicators linked to mixers, relay services or undeclared virtual asset providers. Analysts can review direction, counterparties and customer alignment without reconstructing activity that occurred outside the bank.
This means:
- 🟣SAR narratives become more precise: Reports reflect routing behavior, conversion points and virtual asset involvement with greater accuracy. Law enforcement receives detail that clarifies intent and supports faster follow up.
- 🟣Backlogs become easier to manage: Stronger detection reduces the number of cases that escalate without usable attribution. Analysts can focus effort on activity where origin or routing requires closer examination.
- 🟣Supervisors see more consistent treatment of crypto related movement: Controls demonstrate that institutions can recognize activity that traditional rules cannot surface. Reviews show a clearer view of crypto exposure across the program.
Crucially, better detection improves more than case throughput. It raises the quality of intelligence that reaches law enforcement and strengthens the foundation of crypto AML compliance across the institution.
Regulatory pressures shaping crypto AML compliance in 2026
These improvements are timely, given that supervisors across the United States expect banks to show clearer visibility into crypto involvement inside customer activity. These expectations now extend across institutions that support movement between crypto and fiat:
1. DeFi remains a supervisory focus: U.S. government risk assessments make clear that decentralized finance (DeFi) is a growing area of illicit finance concern, and private-sector actors should align their risk mitigation steps accordingly. In its 2023 DeFi Illicit Finance Risk Assessment, the U.S. Department of the Treasury highlighted vulnerabilities in DeFi services that could be exploited for money laundering and recommended that the private sector take clear steps to address those risks.
2. Mixers continue to draw scrutiny: FinCEN has proposed special measures targeting transactions involving convertible virtual currency mixing, citing concerns about the loss of attribution and routing detail. These concerns align with existing recordkeeping and reporting expectations when crypto-related activity intersects with the traditional financial system.
3. Oversight of undeclared virtual asset providers is tightening: The FATF has reinforced expectations that jurisdictions and financial institutions must identify and mitigate risks arising from virtual asset service provider (VASP) activity, including where such activity is not clearly disclosed. This places greater emphasis on risk-based monitoring to identify intermediary-type behavior that may indicate undeclared virtual asset services.
4. Supervisors also assess how learning carries forward: Recent reports from the EBA highlight that supervisors across the EU are reviewing lessons from confirmed AML/CFT cases — including those involving crypto-asset firms — to refine future supervisory approaches and strengthen detection and oversight.
These expectations shape the direction of crypto AML compliance in 2026. Banks relying solely on internal data will struggle to demonstrate the level of insight examiners now expect.
Bringing crypto activity into view requires shared intelligence
Given everything discussed, you’ll see why bringing crypto activity into view requires shared intelligence. Much of the movement that matters for AML review unfolds outside a single institution’s reach, and the detail that explains origin or intent rarely appears inside customer accounts.
Collective learning changes this. When confirmed cases across the sector strengthen a shared model, investigators see earlier indicators, SARs carry clearer detail and programs can demonstrate the level of insight supervisors now expect.
Institutions do not need to change how data is stored to gain this visibility. They need intelligence that no single environment can produce. Collective model development provides that foundation and strengthens existing controls.
Consilient builds these models with institutions facing the same visibility constraints. The result is a clearer view of crypto exposure and a stronger basis for decision-making. If this challenge resonates with your programme, we’re happy to discuss how institutions are applying collective learning in practice. Talk to us.